Understanding the Challenges of Authentication and Authorization in FHIR for Developers
As healthcare organizations continue adopting the Fast Healthcare Interoperability Resources (FHIR) standard, developers are increasingly tasked with integrating FHIR-based APIs into applications that need to access, share, or analyze healthcare data. While FHIR’s benefits are significant, particularly around data interoperability, the journey toward seamless FHIR integration introduces a unique set of challenges—especially regarding authentication and authorization. For developers, understanding these issues is critical to building secure, scalable, and compliant solutions in the healthcare space.
FHIR at a Glance
FHIR (pronounced “fire”) is a healthcare data standard developed by HL7. It aims to make it easier for healthcare systems to communicate by defining a common structure for data exchange. In essence, FHIR organizes healthcare information into standardized “resources,” like patients, appointments, and medications, enabling efficient data sharing and better interoperability.
While FHIR brings standardization, the sensitive nature of healthcare data means that authentication and authorization processes must be robust to ensure privacy and compliance with regulations such as HIPAA. However, implementing secure access control for FHIR resources is complex, often creating obstacles for developers.
Problem #1: Balancing User and System Authentication
In FHIR-based applications, access to data can be required by different types of users—clinicians, patients, and administrators, for example. Additionally, systems themselves (such as applications or servers) often need to communicate with FHIR servers. Each type of access has unique security considerations, creating an environment where both user and system authentication must be carefully balanced.
Challenge: Many FHIR APIs rely on OAuth 2.0 for user authentication, which is suitable for end-users but can be limiting when handling back-end system-to-system communication. OAuth’s bearer token approach may work for user-centric interactions but can lack the flexibility needed for machine-to-machine interactions, which require more granular control and delegation.
Solution: Implementing OAuth 2.0 with the JWT (JSON Web Token) Bearer Flow and scopes can allow for better access control. However, this approach requires careful configuration and alignment with the organization’s security policies to avoid over-permissioning, which can open vulnerabilities.
Problem #2: Granular Authorization and Scope Management
FHIR supports a diverse set of data types, and different users or systems may require access to specific subsets of this data. Providing broad access to FHIR resources poses a security risk, as users could inadvertently access data beyond their authorization level.
Challenge: Configuring granular access control for FHIR resources can be challenging due to the sheer volume of FHIR scopes that may need management. For example, a nurse may need access only to specific patient data types, while a physician may need broader access. Over-permissioning increases the risk of data breaches, while under-permissioning could impair workflow effectiveness.
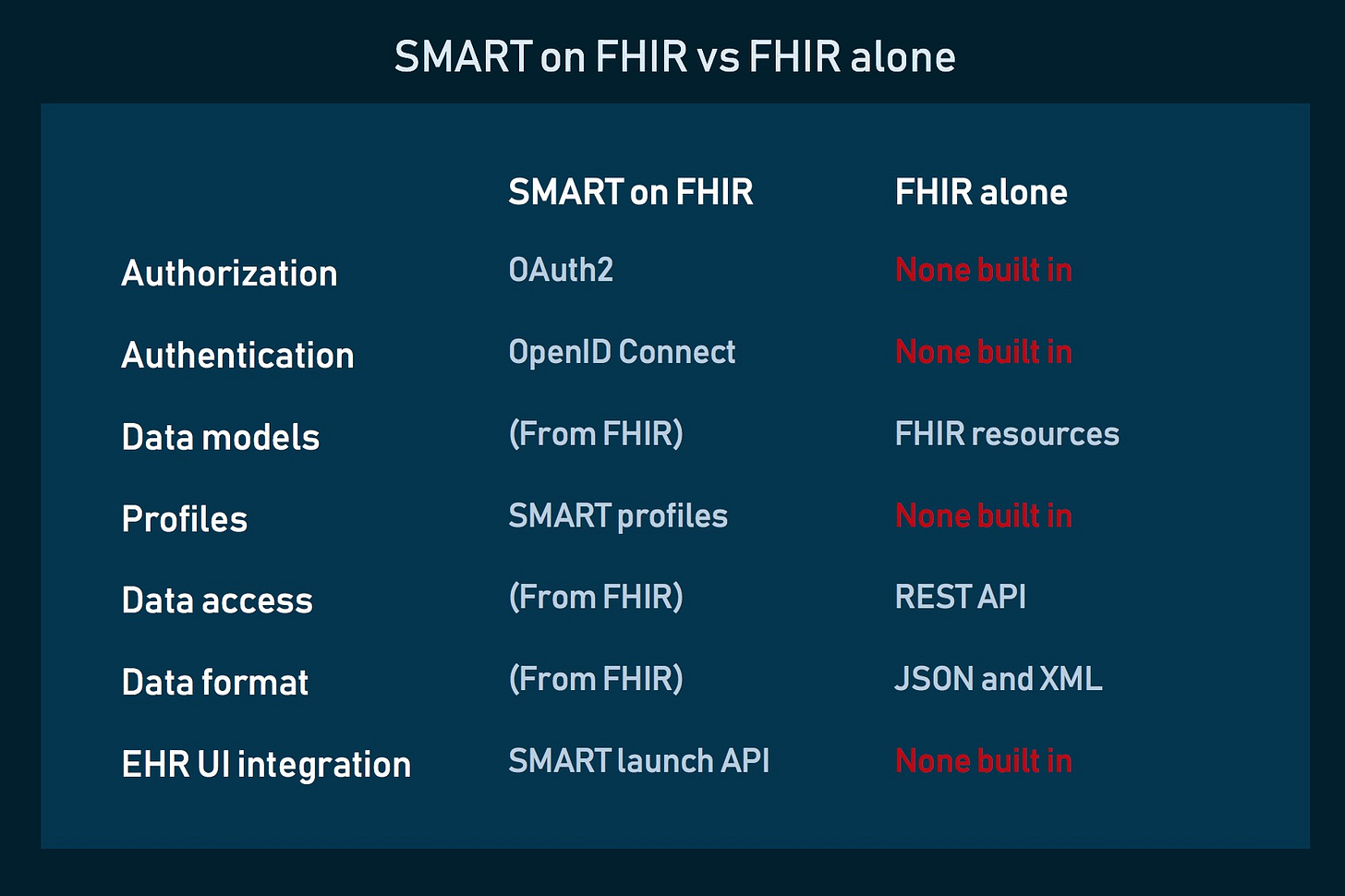
Solution: Using SMART on FHIR (Substitutable Medical Applications, Reusable Technologies), an open standard based on OAuth 2.0, developers can specify scopes that define access levels, allowing more controlled and role-based access to FHIR resources. However, implementing SMART on FHIR requires aligning custom roles and permissions within the application, which may require more complex development and maintenance.
Problem #3: Handling Sensitive Patient Data and Privacy Regulations
HIPAA and other global regulations mandate that healthcare data be safeguarded. However, the open structure of FHIR can inadvertently expose sensitive patient information if security controls are misconfigured.
Challenge: Patient data often exists across multiple FHIR resources. Implementing access controls that protect sensitive fields—such as mental health or substance abuse data—can be difficult. Compounding this challenge, developers need to be aware of compliance requirements in multiple regions, which may have differing levels of data protection mandates.
Solution: Implementing Attribute-Based Access Control (ABAC) can help developers enforce restrictions based on user attributes and data characteristics, such as only allowing clinicians access to certain types of sensitive information. This approach may require additional infrastructure to support dynamic policies and ensure that ABAC rules are aligned with regulatory standards.
Problem #4: Maintaining Session Security in Complex Environments
In a healthcare setting, users and systems often work with large datasets over extended sessions. Managing secure, long-lived sessions is challenging, especially if these sessions require continuous re-authentication, potentially impacting usability.
Challenge: For FHIR applications, token expiration and refresh can introduce complexities, especially if tokens are mismanaged. For example, long-lived tokens can become a security risk if not properly invalidated, while short-lived tokens might disrupt workflows if re-authentication prompts are excessive.
Solution: Implement refresh tokens and session management strategies that align with both security and usability requirements. To reduce disruptions, consider using token rotation or adaptive re-authentication based on risk signals, such as device trust or location.
Problem #5: Lack of Standardization in FHIR API Security Practices
While FHIR provides a robust structure for data, it doesn’t enforce specific security practices, leaving implementation details open to interpretation. This variability can introduce inconsistencies across implementations and make integrating with multiple FHIR systems more complex.
Challenge: For developers, navigating the different security models that vendors or healthcare organizations adopt can slow down integration and create security gaps. Without a consistent approach to authentication and authorization, developers may need to tailor security mechanisms to each FHIR server, increasing development time and complicating maintenance.
Solution: Adopting industry best practices, such as the HL7 FHIR security guidelines and standards like SMART on FHIR, can help create consistency in authentication and authorization. Developing a flexible API wrapper that can accommodate different security models across FHIR servers might also streamline development, though it requires an upfront investment.
Key Takeaways for Developers
Building secure, compliant applications using FHIR demands a thoughtful approach to authentication and authorization. Developers must consider user needs, system requirements, and regulatory standards to strike a balance between security and usability. Key principles to keep in mind include:
Plan for Multiple Access Levels: Define user roles and scopes early to avoid over-permissioning.
Prioritize Granular Authorization: Leverage SMART on FHIR to control access by roles and minimize data exposure.
Use a Layered Security Approach: Employ multiple methods, such as ABAC, JWT tokens, and refresh tokens, to add depth to security practices.
Stay Informed on Regulations: Ensure alignment with local and international data protection regulations for HIPAA, GDPR, and beyond.
FHIR offers an exciting opportunity for developers to advance healthcare data interoperability. However, a secure implementation requires a nuanced understanding of the specific security challenges that come with healthcare data. By addressing these authentication and authorization challenges, developers can create robust, compliant solutions that protect patient data and advance the goals of modern healthcare technology.